The risk of phishing attacks in the crypto space poses a vicious threat to users navigating the information superhighway. What exactly is a phishing attack, and how does it progress from the first email or message to the execution of the scheme?
A phishing attack is a fraudulent scheme where scammers impersonate legitimate entities to deceive individuals into providing sensitive information, such as passwords or credit card details. The attack typically begins with a deceptive email or message that entices the victim to click on a malicious link or download an attachment, leading them to a fake website or software that collects their confidential information.
Latest Phishing Attack Statistics
According to data from Statista, over 963,000 unique phishing websites were identified worldwide in the first quarter of 2024, and two percent is attributed to cryptocurrency. While two percent may seem like a minor fraction, it reflects a continuous trend of malicious entities using crypto to victimize users worldwide. The prevalence of these phishing scams underscores the importance of user awareness and security.
Exploiting Psychology and Technology
Phishing attacks often exploit human psychology and technological vulnerabilities to deceive individuals into revealing personal information, which leads to potential financial losses and compromised security.
According to a blog post by cybersecurity awareness firm MetaCompliance, phishing attacks are effective primarily due to the art of deception mastered by the perpetrators. They use tactics like instilling fear and urgency, exacting authority which leads to trust among victims, using the innate nature of humans to act upon their curiosity and greed, and social engineering.
As phishing attacks have developed, they increasingly take advantage of technological risks. There are numerous phishing methods that scammers utilize through technology. These include smishing (SMS phishing), vishing (voice phishing), social media phishing, AI phishing, and quishing (QR code phishing). When vishing is combined with other methods, it forms what is known as hybrid phishing, a recent trend in phishing attacks.
How to Recognize A Phishing Attack
Phishing messages often create a false narrative to deceive you into clicking links or opening attachments. You might receive an unexpected email or text that appears to come from a trusted source such as your bank, credit card company, or utility provider. It could also be from a payment app or website.
Scammers often pretend to alert you about suspicious account activity or unauthorized login attempts. Others might insinuate there’s an issue with your account or ask you to verify personal information. Sometimes, you might even receive an unfamiliar invoice or a message requesting you to click a payment link that contains malware. Be wary of any text or email promising free gifts, like government refunds or coupons for free items.
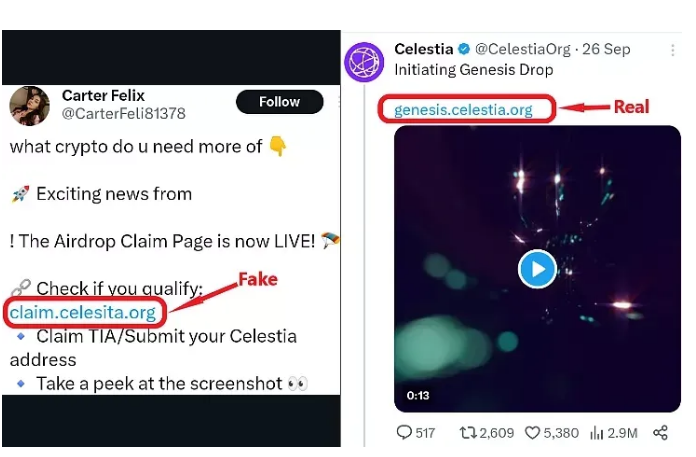
Many phishing scams in the crypto frontier come in the form of fake token airdrops. Fraudsters create imitation websites that look like genuine airdrop campaigns and promote them through a range of methods. These con artists trick users into revealing private information or connecting their cryptocurrency wallets to the fraudulent site. In the end, users never receive the tokens and instead discover their wallets have been drained.
How to Avoid Phishing Attack
The Federal Trade Commission (FTC) offers valuable information for the general public on identifying phishing attempts and protecting yourself from them.
For those in the Web3 space, it can be a bit tricky but there are ways you can safeguard against phishing scams involving cryptocurrency. To secure your crypto assets, never store seed phrases or private keys on internet-connected devices, and create strong passwords for your wallets.
Avoid using public Wi-Fi when accessing wallets and refrain from linking them to unfamiliar websites promising enticing rewards. Always enable two-factor authentication and keep software wallets updated to address potential vulnerabilities. Be cautious with emails and unknown links, and always verify project details through official channels while resisting hasty decisions that could compromise your portfolio.
You can also report any suspected phishing emails or messages to the FTC by forwarding them to [email protected], a contact point used by the Anti-Phishing Working Group, consisting of internet service providers, cybersecurity vendors, financial services, and law enforcement bodies.
Read More
- Truflation Suffers $5 Million Loss in Malware Attack
- 3 Most Common Crypto Scams in 2024 and How to Spot Them
- How to Report Crypto Frauds and Scams to the FBI
Malaya has positions in SHIB, ETH, USDT, MATIC, etc. This article is provided for informational purposes only and should not be construed as financial advice. The Shib Magazine and The Shib Daily are the official publications of the Shiba Inu cryptocurrency project. Readers are encouraged to conduct their own research and consult with a qualified financial adviser before making any investment decisions.










